2022
Useful features in Google Chrome and Microsoft Edge
Learn what are the basic useful features of the internet browsers Google Chrome and Microsoft Edge. See browsers capabilities and security.
The web browser, a gateway to the world of Internet
The web browser is an application for viewing information on the Internet. The information can be of different nature - static or dynamic web page, image, audio file, video, streaming video. The web browser can even be used for video conferencing and broadcasting of your own videos (WebRTC framework), for editing images (Pixlr) and engineering graphics (Thangs). Currently the most popular internet browsers are Google Chrome and Microsoft Edge.
Each information resource needs to be formatted in an appropriate standardized form (for text encoded in UTF8 format, for image in graphic file format webp, JPG, for video file format MP4, WEBM) and to have a unique Uniform Resource Locator - URL.
You move from one web resource (address) to another through the hyperlinks, this is a navigation.
Examples of different web resources on the same domain
Yahoo main website: https://www.yahoo.com/
Yahoo Finance: https://finance.yahoo.com/
Yahoo Entertainment: https://www.yahoo.com/entertainment/
The communication between a web browser and a web resource is most often carried out through a network architecture of the Client-Server model. Its main components include the HTTP network protocol, HTML text formatting language, web pages and web server.
In the beginning was the engine
We use a web browser daily to browse web pages. Did we know that modern web browsers have many more features than browsing pages or videos?! Few people pay attention to new things or improvements in each new version of the web browser.
Chrome and Edge browsers use the Chromium engine, which is open source and anyone can contribute to its development and improvement. The creators of the Chromium project strive to contribute to a better and safer way to surf the Internet. The developers of the project took as a basis another successful project WebKit and built from it a very successful port called Chromium. In the beginning, they integrated several fundamental features such as multiprocessor support, working with the JavaScript version 8 engine and creating a separate process for each open tab in the browser. These basic capabilities led to the creation of a stable and secure web browsers - Google Chrome, and later Microsoft's browser Edge.
Chromium engine, the foundation of Google Chrome and Microsoft Edge internet browsers
Modern microprocessors have several physical cores, as well threads capabilities. An essential part of any modern web browser is the ECMAScript language, better known as JavaScript. With its help it is possible to create dynamic web pages. The developers of Google Chrome have created a new open source high performance engine for JavaScript, written in C++ and running on Windows and Linux operating systems. Several advantages of V8 JavaScript are the compilation of programs to native machine code, efficient placement of objects in memory and fast emptying with the help of "The garbage collector", hidden classes for faster access to properties and methods.

Increased protection in the Chromium engine
Due to the reason for splitting each tab with a separate process, it is possible to limit the process to use system resources only through the main process. This is part of the so-called “Sandbox security mechanism”. This way of managing resources provides an additional layer of protection compared to that of the operating system. For example, restricting the direct use of network interfaces, restricting write permissions on disks. Sandbox conditionally accepts that any code is harmful and limits it. Each tab is also called up on a separate Windows desktop – “Windows desktop object”. Even if there is a breach in a tab, it will make other partitions inaccessible at the operating system level. Another security mechanism is “Job object”, which can be adjusted by excessive use of CPU, memory or I/O traffic.
You can access the task manager in the browser from the three points in the upper right corner. Choose More Tools -> Task Manager.
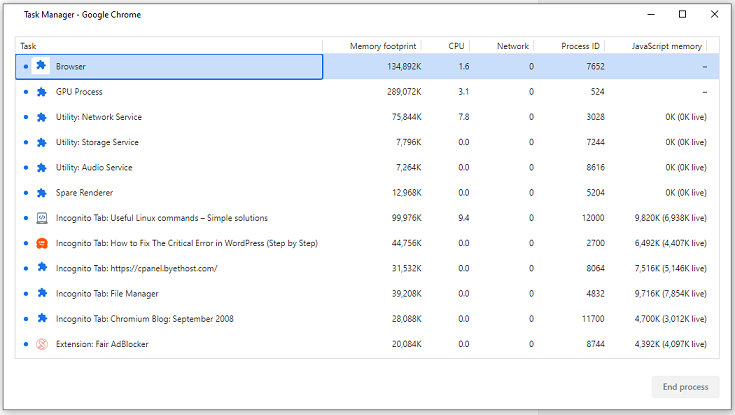
Improved memory management from the Chromium engine
Good memory management is important for efficient system operation. Chromium uses a simple but very effective way to free up RAM. Each open tab in the web browser uses a certain amount of memory. The assumption is that only the active tab needs fast access to memory (in this case the fastest memory is RAM), so the data of the active partition is in this memory. The data for the other inactive tabs (web pages) are saved on the disk in the so-called swap memory (a large file on the disk in which a copy of the data from the real RAM is stored). The engine releases quickly RAM temporarily. Also, when you close a tab, the memory used by it is completely freed.
Plug-ins and extensions
As you may know, modern browsers use plug-ins and extensions to improve the functionality. If you type “chrome://extensions/” in the address bar of Google Chrome browser will see the current installed extensions. Chrome Web Store is a famous place for taking extensions and recently the Edge users can use add-ons from Microsoft Edge Addons Store. These additional modules are implemented in separate isolated processes.
Confidential internet browsing
The communication model described above also adds a method for authenticating a user to the server. The most common way is with the use of cookies. A cookie is a packet of information that is sent by the server and saved to the client computer as a file. The client then automatically sends the cookie to the server with each request during the communication process. The browser may allow or disable the use of cookies. The user can usually choose a setting. As a recommendation, it is good to always use signed cookies. Through the signed cookies the server can inform the client whether the cookie was changed by the client during the communication.
A cookie remains on the user’s computer for use in the next session (cookies have a lifetime), it can also be used only for one session and be deleted at the end of the session.
Google Chrome Privacy Settings
To set cookies policy, click on the three dots in the upper right corner of the window and select Settings -> Privacy and security -> Cookies and other site data.

Of course, we must not forget the strength of the password. A longer password, with more different characters (letters, numbers and special characters) will be more difficult for hackers to crack. Check the complexity of your password with our free password generator.
Cookies can lead to the disclosure of personal data and the anonymity of a user on the Internet. For example, when some commercial companies track user visits to different sites. Some sites contain images called web beetles (which are transparent and one pixel in size so you don’t notice them) that store cookies on every computer that accesses them. E-commerce websites can then read these cookies, find out from which websites they recorded them, and send an e-mail spam with advertisements for products related to these websites. You may have noticed the type of ads that appear on the pages of the websites you visit. The content you view most often matches the ads.
For example, if you often read articles about skin care, facial care, and a healthy lifestyle, you are more likely to be shown advertisements for cosmetics and nutritional supplements.
Microsoft Edge Privacy Settings
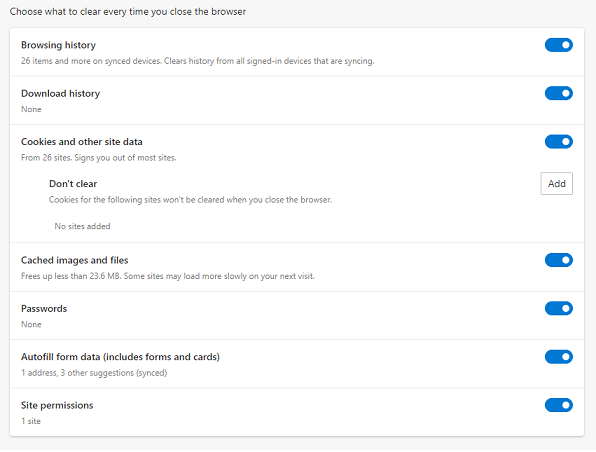
For the privacy settings for Microsoft Edge you can also click on the right upper corner on the dots and choose Settings -> Cookies and site permissions. To clear all cookies and site data when you close Microsoft Edge, go to Clear browsing data on close. I recommend to enable all options or at least Browsing history and Cached images and files. These enabled options will also prevent your computer from jamming with unnecessary files. The large number of files in the system often leads to a drop in performance. You can also choose to manually clean for certain periods of time.
Google Chrome Incognito and Microsoft Edge InPrivate mode
You can always open a confidential browsing window without having to change the settings. Click on the three points again at the top of the window and select New incognito window for Chrome or New InPrivate window for Edge.
Chrome web browser will clear:
- Your browsing history.
- Cookies and site data.
- Information entered in forms.
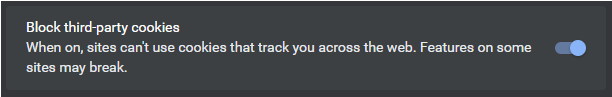
For a higher degree of privacy you can Block third-party cookies.
- Deletes your browsing information when you close all InPrivate windows.
- Saves collections, favorites, and downloads (but not download history).
- Bing does not associates the search queries with you.
For a higher degree of privacy you can use “Strict” mode of tracking prevention.

Forced startup in incognito/private mode
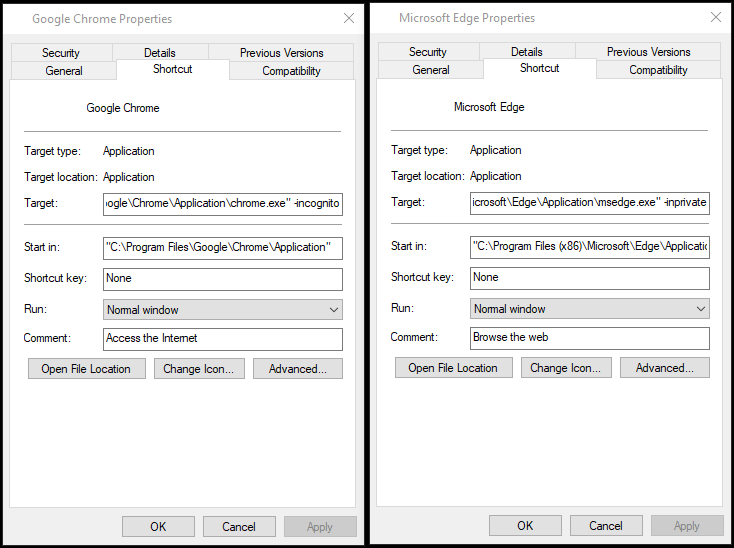
You can set your web browser to always run in private with a small hack. Right-click the web browser icon on the desktop and select properties.
At the end of the Target field, add for Chrome -incognito and for Edge -inprivate.
Conclusion
The main feature of Google Chrome is that it has lots of extensions which allow users to customize their experience. Microsoft Edge also has some cool extensions as well, and has a lot more customization options than Google Chrome. Microsoft Edge has more built-in security features. Google chrome has better user interface design and security features.
Contact
Missing something?
Feel free to request missing tools or give some feedback using our contact form.
Contact Us